Introduction
SSH is program that allows for secure remote access to another computer. All traffic through the SSH connection is encrypted. That's great! It's an excellent replacement for Telnet, which is insecure, and shouldn't be used anymore. But logging in is still susceptible to brute force attacks.
However if one uses RSA keypairs, an attacker would have to have the private key in order to login to your system, even if they had the right password. It is also possible to have keypairs for passwordless authentication; however that is better suited for automated tasks (bash scripts) that are executed via cron. And y0u really have to safegaurd those keys!
I'll show you how to use RSA keypairs with OpenSSH. I will assume that you already have OpenSSH Server installed, configured, and are able to login remotely with SSH using the standard authentication method. I'm doing this on OpenSUSE 11.1, so things may be different on your distro or version of SSH. So let's get going!
Generate Keypairs
On your Linux computer (server or client), enter this at the command prompt (as your user)
- ssh-keygen -t rsa
user@linux-ftim:~> ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
The default should be fine, so just press Enter
And now we're asked for a passphrase. Enter and confirm your password. You could choose not to enter a password, but again, unless you're running automated scripts or have a specific reason to, it's not a good idea to do that.
The response
user@linux-ftim:~> ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
Created directory '/home/user/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/user/.ssh/id_rsa.
Your public key has been saved in /home/user/.ssh/id_rsa.pub.
The key fingerprint is:
7f:1b:12:15:15:7f:ce:f0:83:fa:87:a5:36:77:d8:76 user@linux-ftim
The key's randomart image is:
+--[ RSA 2048]----+
| ..o. |
| . . |
| . . o|
| . .=.|
| S . . .+|
| . .. ..|
| o.o +o |
| o.B.oE|
| o.+.o|
+-----------------+
user@linux-ftim:~>
Now we have a public key (~/.ssh/id_rsa.pub) and a private key (~/.ssh/id_rsa). The public key is what will be installed on the SSH server. The private key is the key that you take with you and use on the computer you will be loggin in from.
Configure the Client
Edit the /etc/ssh/ssh_config file. This controls how ssh is employed from the command line. Make sure the following lines exist, and are uncommented:
/etc/ssh/ssh_config
IdentityFile ~/.ssh/id_rsa
Protocol 2
Configuring the Server
This will control the SSH server daemon
/etc/ssh/sshd_config
Protocol 2
PubkeyAuthentication yes
Using the Keypair
Take the public key (id_rsa.pub) and copy it into the ~/.ssh directory on the server computer. You'll have to add the new key to a file called authorized_keys.
- cat id_rsa.pub >> ~/.ssh/authorized_keys"
- chmod 600 ~/.ssh/authorized_keys
Using Putty on Windows
You can also generate RSA keypairs using Putty on Windows. However, I'm imagining that using Putty on Windows will be an afterthought after several servers and/or client computers will already be configured with existing keypairs. That's how we're going to proceed here.
Getting Putty
Go to either http://www.putty.org, or directly to the download page. The version I'm using is 0.60, which is the lastest as of this writing. Install it per the installation guidelines. I used putty-0.60-installer.exe, but you can also download individual components. You'll need putty.exe, and puttygen.exe.
Copy your private key, id_rsa, to the Windows computer.
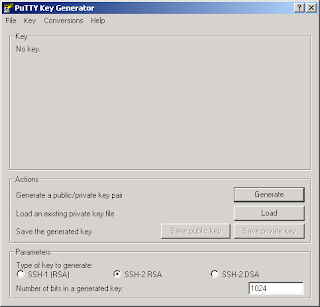
Open PuTTYgen. Select "Conversions" from the menubar, and click on "Import key".

Select your id_rsa key and click open.

Enter your passphrase for the key, and click OK

Now we're ready to work with the key. Putty stores keys in its own format, for whatever reason. But hey, we can work with that!

Now click on "Save private key", and give your key a name. Now you can close the key generator.
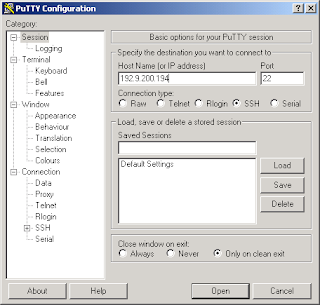
Now, open PuTTY. Enter the hostname or IP address of the computer you want to connect to.

On the left side, under Connection, expand SSH and click on Auth. Under Private key file for authentication, enter the path to the PPK file, or click on Browse and select it. If you c,lick Open, you'll continue to connect. Or if you go back to Session, you can save the configuration and use it later. This is particularly handy if you manage several servers with different keys, different SSH ports, etc.

You will get the security alert, saying that you haven't connected to this computer befire. Click on yes to contine.

Enter your username. You should get a prompt telling you that you're using a public to to authenticate, and asking for a passphrase, not a password. Enter your passphrase, and you're in!!
-- DRH
No comments:
Post a Comment